We envision azure ad as the key to embracing a zero trust security model enabling secure application access and greater productivity across users apps and devices.
Gartner magic quadrant encryption key management.
Develop an enterprisewide encryption key management strategy or lose the data published.
In this report analyst ramon krikken discusses drivers risk and requirements.
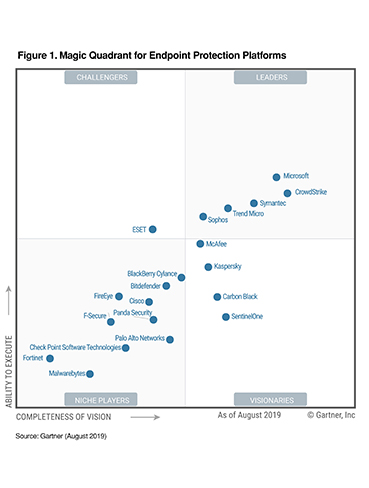
Leaders visionaries niche players and challengers.
Most organizations lack proper frameworks for encryption use.
19 december 2017 id.
22 january 2014 id.
Challenges in transportation such as talent availability visibility and volatile delivery requirements are increasing the need for technology.
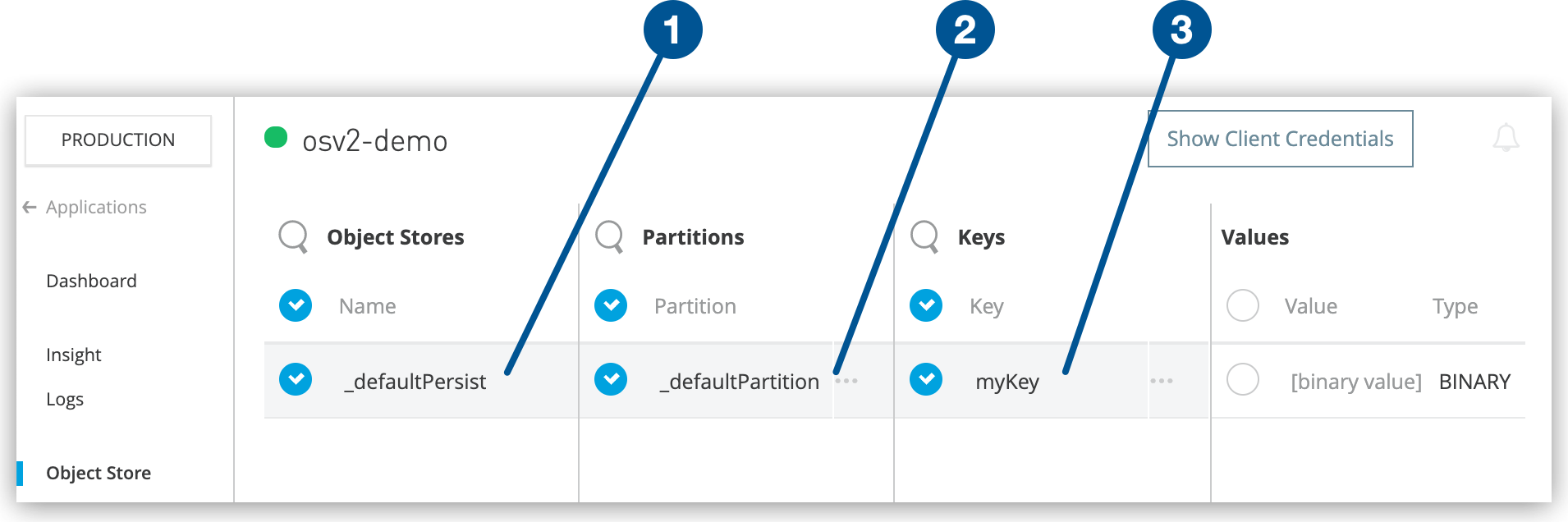
Ekms functions and selection.
Gartner magic quadrant for transportation management systems summary the transportation management system market continues to grow globally.
Gartner magic quadrant research methodology provides a graphical competitive positioning of four types of technology providers in fast growing markets.
Develop an enterprisewide encryption key management strategy or lose the data published.
As companion research gartner critical capabilities notes provide deeper insight into the capability and suitability of providers it products and services based on specific or customized.
As the use of encryption in an enterprise increases so do the potential headaches surrounding management of the associated cryptographic key materials.
30 october 2017 id.
Effective encryption key management published.
The organization s it security leaders must create an encryption key management strategy when deploying cryptography or risk losing the data.
David mahdi brian lowans summary most organizations planning data encryption deployments lack encryption key management strategy which increases the risk of data loss.
Consistently landing in gartner magic quadrant for the past four years tells us that we re executing on our vision and making a difference for you our customers.
Enterprise key management systems ekmss are designed to address problems with managing cryptographic keys for data at rest.
As the market for endpoint encryption grows the race for the best product and biggest market share grows increasingly competitive.
Key management as a service exposes different risks to data in public clouds published.
In an impressive display of superiority symantec ranks as the leader for endpoint encryption in gartner s 2016 magic quadrant 2016 for the second time in a row.
Erik heidt summary enterprises should focus on establishing centralized governance and oversight over key management operations while having cryptographic operations performed by teams with appropriate technical skills.